Hikvision nastavení s Gmailem
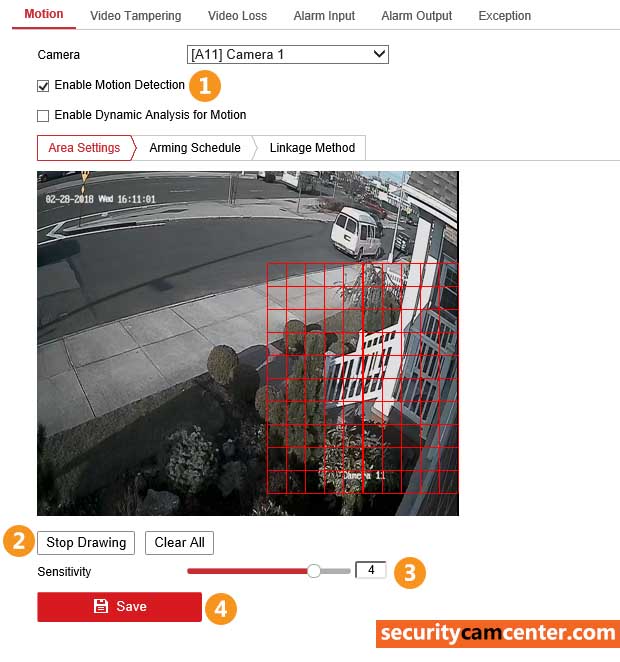
If you’d like to get email alerts, we recommend using a Gmail account since it’s free, secure, widespread, and easy to configure. You can use other email providers as well (such as Outlook, Yahoo, etc.), the steps are similar. NOTE: As…